Zigging Through Cybersecurity: Leverage the Power of Zig for Secure Code
In the constantly evolving landscape of cybersecurity, every tool in a developer
ChatGPT's Hidden Security Risks Gamble With Business Data - Converge Technology Solutions

Leveraging Data Science For Enhanced Cyber Security, by Auxin

User Clip: markey

The OWASP Top 10 for LLMs: A Light-hearted Look at Serious Security

Remote Exploitation w/ Python3: Socket Reuse

What are the Goals of Cyber Security? Best Explained - 2023

Exploring Zig: A Modern Programming Language

Uncovering Malicious Python Packages on PyPI Repository

Zigging Through Cybersecurity: Leverage the Power of Zig for Secure Code
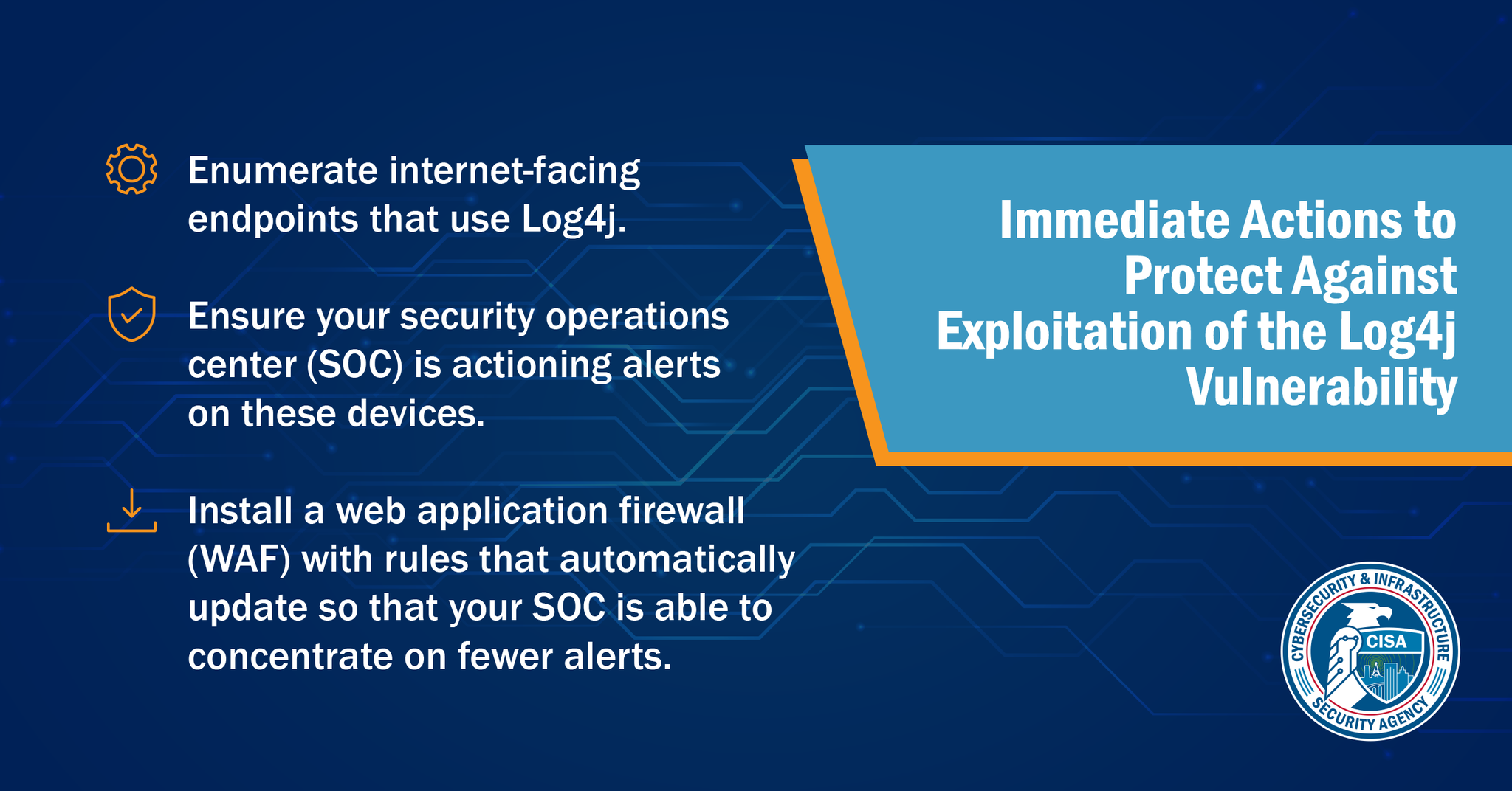
Log4j Vulnerabilities Guide : 3 Steps to Protect Yourself & CISA Recommendations - All Articles - CISO Platform

The Importance Of Cyber Security Within Your Organization

6dfvdfvd by oiojiwerwer - Issuu