Threat Hunting - Simplifying The Beacon Analysis Process - Active
In part one of this two-part series, I described what is involved with performing a beacon analysis and why it is so important […]

LDAPFragger: Bypassing network restrictions using LDAP attributes, NCC Group Research Blog

Detecting Beaconing Attacks by Advanced Threat Hunting
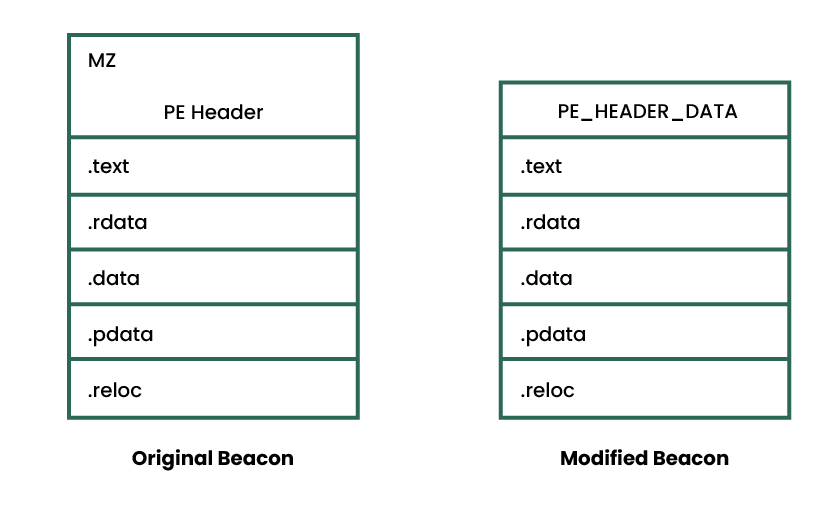
Revisiting the User-Defined Reflective Loader Part 2: Obfuscation and Masking

Threat Hunting Beacon Analysis

Threat hunting: Part 1—Why your SOC needs a proactive hunting team

Blowing Cobalt Strike Out of the Water With Memory Analysis
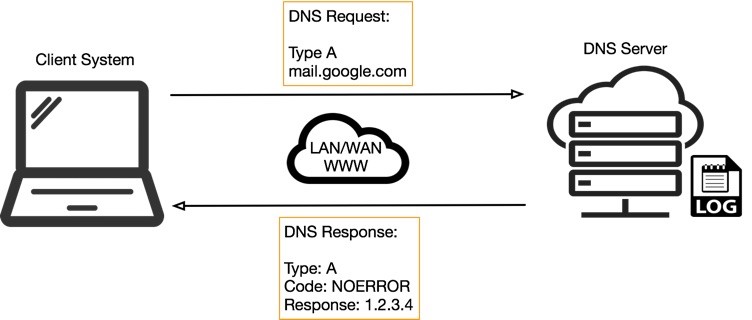
DNS Tunneling: how DNS can be (ab)used by malicious actors

What is Cyber Threat Hunting? [Proactive Guide] - CrowdStrike

How to Avoid the OWASP Top 10 List of Vulnerabilities
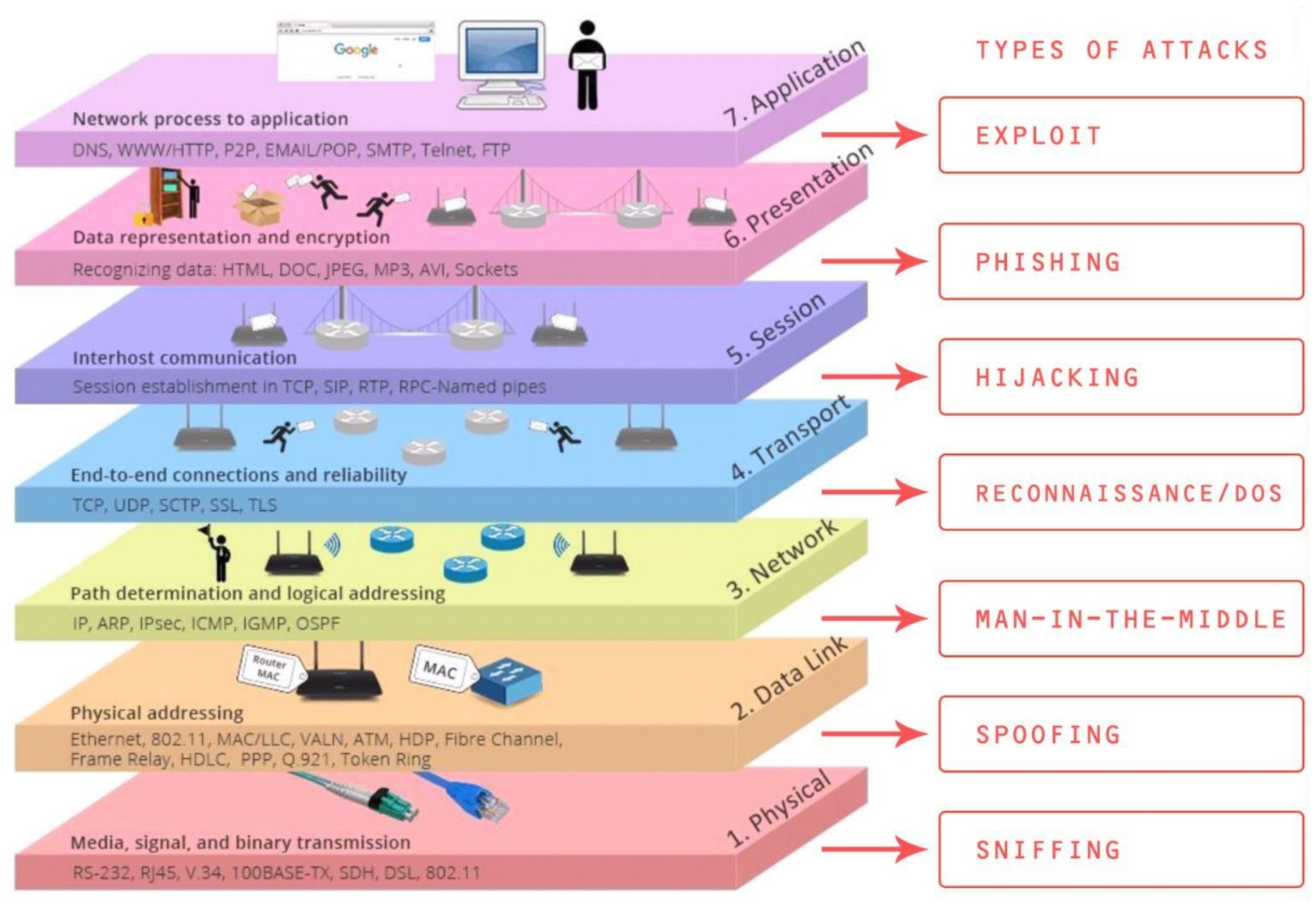
Symmetry, Free Full-Text

New sophisticated email-based attack from NOBELIUM
Mining data from Cobalt Strike beacons, NCC Group Research Blog
What is Threat Hunting? Threat Hunting Explained